top of page
Security.BitMint.com
Randomness is a trusted shield against smarter and better equipped adversaries
Search


Innovative Security
It is the only security that will withstand your innovative threat C yber security is a big project for a big corporate data world. It is designed, built and maintained like a big project. Alas, a typical big project is designed and built with an operational end point, striving for perfection and associated stability, routine, trouble free use. By contrast, cyber security projects are fundamentally different. For them a stable end point is where their vulnerability begins. S
Gideon Samid
2 hours ago4 min read


HIPS: A Cryptographic Protocol that Can Change the Course of History
We have lost the freedom to talk to our cyber neighbors privately. Yes, we can send an encrypted message, but by this we raise a flag: Hey adversaries! -- Look who I am talking to, and how much, and how frequently. And yes I have the key to decrypt it, but I would not share it with you unless you threaten me or coerce me -- that is not privacy. HIPS is! Imagine that you can talk to any resident of cyberspace, without leaving a trace, without even raising suspicion that this c
Gideon Samid
Dec 15, 20253 min read


DoW new PQC policy Overlooks new US Security Technology, used by Adversaries
The Department of War just announced that it phases out pre-shared keys (PSK) quantum resistant cryptography (PQC). On its face this is a prudent policy decision. Pre shared keys live long, and the longer a key lives the greater the chance for it to be compromised. Alas, this bold policy decision leaves the DoW to rely either on unproven NIST or NSA sanctioned key generation algorithms, or on shared qbits. The first relies on an adversary who is not smarter than expected, and
Gideon Samid
Dec 11, 20252 min read


"Weak Keys" The Unmentioned Risk Shared by NIST PQC Candidates
The quintic polynomial cannot be solved -- as Abel and Galois have shown. Which only means that there are instances of a five degree polynomial for which no formula offers a solution. Which in practice means that there are countless instances of the quintic, subscribing to a particular class, for which there is a solving formula. The same for NIST PQC ciphers -- even if they had (which they don't) a proof of no general solution, they are all plagued by the reality that key
Gideon Samid
Oct 31, 20252 min read


Cover Your Cyber Nakedness with a Fig Leaf of Randomness
We live in cyberspace, and thereby expose our whims, proclivities, secret desires, ambitions, love, hatred, emotions. Modern AI sees us...
Gideon Samid
Jul 19, 20251 min read
A Ciphertext as a Deterrent
Elastic encryption ciphertexts deter cryptanalysts from cracking them. New feature in the on going cyber war. An elastic ciphertext...
Gideon Samid
Jul 7, 20251 min read


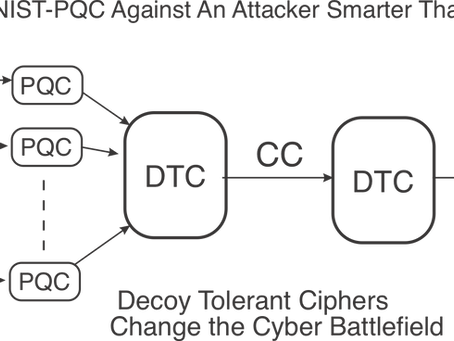
Fortifying NIST-PQC Against An Attacker Smarter Than Expected
The nightmare of every cryptograher is an attacker using. surprise mathmatical insight to crack the code. The NIST-PQC cryptographer is...
Gideon Samid
Jul 4, 20252 min read


Elastic Encryption: AI Empowered Cryptology
Abstract: Artificial Intelligence will associate a ciphertext with a set of plausible plaintext message candidates for the one message...
Gideon Samid
Jun 27, 202531 min read


The Future of Cyber Space Hangs in the Balance -- Can a New Cryptography Save Us?
Life in cyberspace shapes up as a paradise for the powers that be, blanketing us the people with invasive surveillance, administered...
Gideon Samid
May 28, 20254 min read


The Biggest Milestone in the History of Cryptography is Quietly Upon Us
Mathematical Insight is No Longer an Advantage Abstract: Throughout its stormy history and remarkable track record, cryptography was...
Gideon Samid
May 15, 20257 min read


AI Accelerated Brute Force Cryptanalysis: Bigger Threat than Quantum
Plain brute force cryptanalysis is destined to check on average half the possible secret keys that guard any cyber secret, including...
Gideon Samid
Dec 7, 20241 min read


Proof-of-Secrecy (POS) Cryptography
To say that cryptography today is constituted on arrogance and hubris, is to risk being summarily dismissed by anyone who counts. And it...
Gideon Samid
Nov 27, 20242 min read


Cryptography and Privacy: An Impactful Milestone Ahead
Privacy is back in the hands of the user, dial it up as high as you please! Freedom Wins!
Gideon Samid
May 24, 20235 min read


Will AI Demolish Cryptography?
In the 70s of the last century a thousand years old premise of cryptography was challenged. The idea of using the same key to encrypt a...
Gideon Samid
Apr 12, 20233 min read


AI is here, Cryptography! Are you ready?
It has shaken every other field. It is coming for you (or rather for us, I should say). It is opening a new line of attack, one we have...
Gideon Samid
Apr 7, 20232 min read


How did Russia get under our Cyber Skin?
US Intelligence was stymied by Stalin's spies who used an American super cipher, which we dismissed... It was the notorious Vernam...
Gideon Samid
Apr 18, 20222 min read


Family Key: Interchangeable Symmetric Keys: a new Cryptographic Paradigm
In the current crypto paradigm a single secret key transforms a plaintext into a ciphertext and vice versa, or at most a different key is...
Gideon Samid
Mar 29, 20212 min read


High Profile Spending Espionage
Silent Reading of Credit Card Spending History of High Level people is Sold to their Rivals -- a new line of Industrial Surveillance....
Gideon Samid
Mar 4, 20211 min read


Why does US Cyber Security Fail? Hackers Wakefulness Defeats Establishment Inertia
It was a huge NSA led cyber investment to massively scan world-wide communication to zero in on encrypted traffic to be further looked...
Gideon Samid
Jan 17, 20214 min read


Drones are the fastest growing Mode of Transportation -- the Fastest Growing Hacking Target Too
Hacked drones smashing into windows, bumping into people, peeping through sunlight windows... this is the troubling scenario for the not...
Gideon Samid
Dec 29, 20201 min read
bottom of page